Abstract
The idea of a program that replicates itself may have originated in the early days of computing, when programmers amused themselves by trying to write the shortest program that prints itself. In today’s world every organizations and individuals using computer and internet need to have a wide-ranging virus protection policy to combat the growing threats of computer viruses by means of anti-virus. This is due to the fact that a computer virus may corrupt or delete data on a computer. Computer viruses also spread by using downloads on the Internet. Computer viruses can be hidden in pirated software or in other files or programs that you may download. Boot sector viruses take advantage of the boot process of personal computers (PCs). Because most computers do not contain an operating system (OS) in their read-only memory (ROM), they need to load the system from somewhere else, such as from a disk or from the network (via a network adapter).
Keywords: BSV (Boot Sector Virus), FAT(File Allocation Table), OS(Operating System), WOS(Windows Operating System), MBR(Master Boot Record), Bootstrap Loader, RC(Recovery Console), BSOD(Blue Screen of Death), PBS(Partition Boot Sector).
INTRODUCTION
A biological virus (from the Latin for poison) is a shell filled with genetic material that it injects into a living cell, thereby infecting it. The cell then starts manufacturing copies of the virus. A computer virus behaves similarly. A computer virus is a malware, when executed, try to replicate itself into other executable code; when it succeeds, the code is said to be infected. The infected code, when run, can infect new code in turn. The self-replication into existing executable code is the key defining characteristic of virus. So it is the program that can copy itself and infects a computer without permission or knowledge of the user. In this paper we have discussed only about a special type of virus known as the BOOT SECTOR Virus. Before going in depth, the working definition of virus should be as under:
It is capable of propagating between computers on a network. This is the most important attribute of a computer virus and it is what distinguishes a virus from other types of malicious software.
It installs itself in a host computer without the owner’s knowledge or consent.
It has the potential to damage software on the host by altering or deleting files.
It can prevent legitimate users from using some or all of the computer’s resources.
In general it embeds itself in an executable file (its host), such that when the file is executed, the virus is also executed. The virus is hidden inside the host.
Boot Sector Viruses
A boot sector virus (BSV) is a computer virus that resides in the boot sector of a disk. Each time the disk is mounted, the boot sector is read and executed, causing the virus to be executed. The boot sector of a disk is normally the first sector of the disk, as its format depends on the operating system. Often, the boot sector occupies more than one disk sector. It may also include a table with information about the disk itself (such as maker, date of manufacture, model and serial numbers, size and number of tracks) and on the various partitions of the disk. The directory of a disk reflects the file structure of the disk and provides the user with all the information that’s normally needed about the files. However, in addition to the files listed in the directory, there is at least one program that’s not listed there. It resides in the boot sector of the disk and this is the program executed each time the disk is mounted and is responsible for OS Loading further.
Boot Sector Loader
A computer operates by executing a program. A computer without a program can do nothing. This implies that a newly-bought computer must have a program built into it. This program is called the bootstrap loader and is stored in read-only memory (ROM), which is nonvolatile (it keeps its content when the power is turned off). Each time the computer is booted (started or restarted), it executes the bootstrap loader. This short program reads the first part (the kernel) of the operating system from a disk or a CD and starts it. The kernel then reads the remainder of the operating system and stores it in memory.
The point is that the bootstrap loader is stored in ROM and is difficult and time consuming to replace. It should therefore be general and be able to load any version of any operating system—past, present, and future—from any bootable device. Currently, PCs run Windows or Linux OSs and each of these goes through newer versions all the time. Another complication arises because a bootable volume may be divided into several partitions, each of which may have a different operating system. Thus, the bootstrap loader should not be limited to loading just one type or one version of the operating system. The bootstrap loader starts by looking for a bootable volume (disk or CD) and it follows simple rules to determine which bootable volume to select when it finds more than one. The bootstrap loader then reads the volume’s master boot sector, loads it in memory, and executes a jump instruction to its beginning of boot sector. The boot sector contains a short program called the master boot record (MBR). This program knows about the various partitions of the volume and how to read the boot sector of each. It locates all the operating systems in the various partitions of the volume and lists them for the user to select one. Once a specific operating system has been selected on partition P, the MBR reads the partition boot sector (PBS) of P and executes it. The short program of the PBS reads and loads the kernel of the operating system, and it loads the rest.
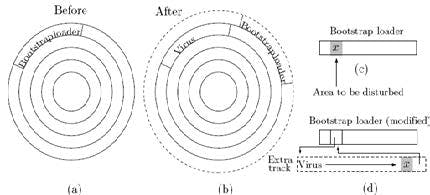
The best place for a virus is in the bootstrap loader; because this program is the very first one to execute but it is difficult since this loader is made in a factory and its content is permanent (modern bootstrap loaders have firmware and can be modified when new versions of the operating system are released). The next best place for a virus is the MBR or one of the PBSs. A virus that’s hidden in these locations is called a boot sector infector or BSI. The precise organization of a disk depends on the operating system. A disk may have one bit in its boot sector informing the bootstrap loader or other operating system routines whether the disk is bootable or not. Alternatively, a nonbootable disk may have a program in its boot sector and the operating system may have to execute this program to find out whether the disk is bootable. In the latter case, a virus can hide in the boot sector of nonbootable disks. An important point to consider is that the virus doesn’t have to be physically located in the boot sector. The boot sector contains a loader program that reads other operating system routines and stores them in memory. It is therefore enough for the virus writer to write the virus as a file on the bootable disk and to modify the loader to load the virus from the disk while it loads other programs. Even though the virus is written on the disk, it may not appear in the disk directory. It may also be written in an extra track, especially formatted on the infected disk. Disk utilities and anti-virus software read the number of tracks from a table in the disk itself, and therefore know how many tracks to read and examine. An extra, undocumented track, either close to the edge of the disk or between existing tracks, may be an ideal place to hide a virus.
Figure 1 illustrates two variations on this technique. Part (a) of the figure shows a bootstrap loader located in track 0, sector 0 of a disk. Part (b) shows how a virus may move the original loader to a new, extra track and install itself instead of the loader. Part (c) shows another bootstrap loader that’s going to be disturbed a little (in part d) by the incoming BSV virus. The virus installs itself in the new track. It cuts a small part (x) of the loader, moves it to the end of the virus, and replaces it with a JUMP to the start of the virus. When the virus completes its execution, part x is executed, and then control is transferred to the bootstrap, to finish its execution.
IMPLICATIONS OF BOOT SECTOR VIRUS ON WINDOWS OPERATING SYSTEM
Boot sector viruses gain complete control of the master boot record or the DOS boot sector by replacing the operating system contents with that of its own. This allows the virus to spread fast and cause damages like to redirect disk reads, moving or damaging the master boot record to another location which further results the system to crash. The hard disk drive is partitioned into logical partitions. Each drive consists of four logical parts--Boot Sector, File Allocation Table (FAT), Directory and Data space. Of these, the Boot Sector contains information about how the disk is organized. That is, how many sides does it contain, how many tracks are there on each side, how many sectors are there per track, how many bytes are there per sector, etc. The files and the directories are stored in the Data Space. The Directory contains information about the files like its attributes, name, size, etc. The FAT contains information about where the files and directories are stored in the data space i.e. it is the index of all the files on the drive. When a file/directory is created on the disk, instead of allocating a sector for it, a group of sectors is allocated. This group of sectors is often known as a cluster. How many sectors together form one cluster depends upon the capacity of the disk. So, FAT contains information about the space used by each individual file, the unused disk space and the space that is unusable due to defects in the disk.
Boot sector virus spreads in the WOS by either by infecting the Master Boot Record (MBR) so that system is unable to boot itself. Another type of boot sector virus makes copies of itself to 3 blocks on a floppy diskette or hard drive and these blocks are marked bad in the File Allocation Table (FAT), so that they cannot be overwritten. Being so destructive in nature, virus completely destroys the information or data present on the hard disk. After the virus has encrypted the entire disk, the only way to get rid of this virus is to re-format the system. But, formatting removes all the data from the hard drive, which ultimately results in data loss.
One may receive a "Stop 0x0000007B" error message (often known as Blue Screen Of Death or BSOD), Figure(2), if computer is infected with a boot-sector virus which means "inaccessible boot device": Windows is not able to read from the device it is supposed to be booting from. That device in general be hard drive - but if one getting this during Windows installation, it could be something wrong.
Examples: Michelangelo, Disk Killer or Ogre, Brain, W32/ (A boot-sector virus infects various versions of the 32-bit Windows operating system).
On the other hand if everything is well in WOS then Loader with help of assembly instruction dw 0xAA55 simply puts the hexadecimal word "0xAA55" in memory, and org 0x7C00 puts the current memory address at 0x7c00, so any instruction after this will start at 0x7c00(assuming 16-bit storage) to load WOS.
(The hex value 0xAA55 is used as a key signature for boot sector, that mark it the active partition to load the OS startup code in memory to load boot sector in memory. dw 0xAA55 is the signature found at the end of the boot sector .The value 0x7C00 is the memory location where the boot sector code is loaded by the BIOS to execute the code.)
Protection:
- To protect WOS from any type of virus infection and possibly recover is to have anti-virus software on computer.
System using versions earlier to Windows XP use fdisk /mbr command, to fix the boot sector error, in MS-DOS during booting process. It should be noted that in WOS repartitioning with Fdisk does not rewrite the MBR and can only create re -partitions. But by using additional parameter called /mbr makes to write the master boot record to the hard disk without altering the partition table information using BIOS calls.
From Win XP onwards, where NTLDR is a boot loader, essential disk maintenance tools have been moved to the Recovery Console, which is available when one boot it from the original XP CD. Once accessed in the RC, use the command FIXMBR, which is the equivalent of fdisk /mbr (it writes a fresh copy of the MBR).
PROBLEMS IN BSV DETECTION
The possible problems in locating the BSVs are as under:
BSV is so hazardous that it can exploit interrupts to hide itself and also can modify one of them. The task to detect it is too difficult. Suppose somebody wants to locate this virus on the disk. Then he has to read the boot sectors and examine them, but the (memory resident) virus can (and normally does) defeat that. The virus modifies some of the interrupt routines and also the part of the operating system responsible for disk input/output (in the old DOS operating system this part was called BIOS). If this is done properly, the virus is invoked by the BIOS routines each time a program wants to read a sector. The virus then examines the read command, and if the command wants to read a boot sector (sector 0 of track 0), the virus changes the disk address of the read operation from (0, 0) to where it has hidden the original boot sector. An associated problem faced by this type of virus is secondary infection. Before infecting a new disk, the virus has to make sure the disk hasn’t been infected already..Thus, the virus must contain a unique fingerprint or signature.
The virus can hide the original boot sector in one of the free sectors (if any) on the disk. The virus uses some of the free sectors, removes them from the chain, and declares them bad. An alternative is to create an extra cylinder on the disk. The capacity of a cylinder is larger than what a virus needs and its presence cannot be detected by the operating system because it receives the number of cylinders from the disk’s header. Modern hard drives have large capacities in a small volume, so any added cylinder would be too close to the edge of the disk and would be unreliable. Older disks, both hard and floppy, were more amenable to this technique. It takes an experienced virus detective to foil such a sophisticated virus.
The BSV should establishes itself in memory (if it is not located there already) by modifying one or more interrupt-handling routines, especially the routine that is called when a removable disk is inserted. This way the virus will be able to infect the boot sectors of new disks inserted into the computer.
The computer owner can prepare in advance a copy of the boot sector, and later compare it to the boot sector of a suspicious disk. However, a well-designed virus can often defeat this simple check because of the way disks are read and checked.
Furthermore in order to read the boot sector and print it, display it, or compare it to a list of instructions, a program is needed. The program should work by invoking operating system routines (sometimes called basic input/output system or BIOS) and the point is that the program can able to modify these routines. Specifically, the routines can be modified such that when they are asked to read the boot sector, they will provide a copy of the original, non-infected sector that had been hidden on the disk by the virus. The security expert can take the suspect disk to another computer and try to read the boot sector there, but the virus may be executed from the boot sector (and modify the BIOS routines) as soon as the disk is inserted into the new computer. The disk should therefore be read in a different type of computer or in the same platform but under an operating system that the virus doesn’t recognize. An alternative is for a security expert to write low-level disk routines, similar to the ones used by BIOS, and read the disk with these routines.
CONCLUSIONS
A boot sector virus embeds itself in the boot sector of a disk (floppy, zip, or hard disk) or a CD, and becomes memory resident when the computer is booted from the disk (if the disk is bootable) or when the disk is inserted into a disk drive and is read. The virus stays in memory while the computer is on, so it can infect any disk mounted in the computer. And this is the fact that this virus that it is easy to detect, because it (or at least its first part) is located at the same position on every infected disk. Furthermore, since BSV can infect hard disks so one has to avoid its propagation by using infected removable disk (a floppy disk, a zip cartridge, or other removable media) from computer to computer. Some BSV itself does not locate themselves in the boot sector but hides elsewhere (generally in extra track) on the disk and be loaded by the loader in the boot sector when the disk is mounted. Such a virus modifies the boot sector, but only in an insignificant way, by adding a few instructions that load the virus. The virus itself may be hidden in an extra track or in unused disk space but in this case the virus may be erased when a new file is written on the disk.
Most programs (executable files) never change their content. The program does not modify itself when executed. The same is true for the boot sectors on disk drives. Such sectors contain programs that load files from the disk, and those programs are always the same (they change only when new versions of the operating system are installed). It is therefore relatively easy to write an anti-virus program that will scan all the executable files on a disk, store their sizes in a table, and use this table in future executions to locate those executable files whose sizes have changed. This anti-virus program should be run periodically, to notify the user of any changes. In WOS, DOS 6.22 Msav.exe will clean the MBR and RAM of the computer. However Mac OS and Linux both have safeguard built in to protect you from these problems.